One process that has been clearly described in the previous post for conducting active reconnaissance is Enumeration. One important activity is how can we reveal […] Read More
Writeeeeee… Before Forgotten

One process that has been clearly described in the previous post for conducting active reconnaissance is Enumeration. One important activity is how can we reveal […] Read More
In the previous post, we have talked about passive reconnaissance to find information about the network. It was called passive reconnaissance because we did not […] Read More
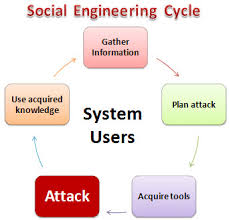
Besides engineering way, there are many ways to compromise the network without doing something technical; we always mention it with social engineering attacks—many tactics for […] Read More
In IT world, sometimes the developer is in ‘not good’ condition when he is doing his job, Maybe he is having problems in his family, […] Read More

PHP has a lot of functions which can be used to crack your server if not used properly. You can set list of functions in […] Read More