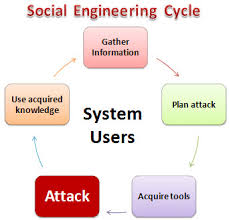
Besides engineering way, there are many ways to compromise the network without doing something technical; we always mention it with social engineering attacks—many tactics for doing social engineering-and usually related to the psychology of the user.
Basic Components of Social Engineering Attacks :
- Target evaluation
Assess target’s susceptibility to attack and their awareness of cybersecurity - Pretexting
Communicate a lie or incomplete truth to get the victim to believe a falsehood. - Psychological manipulation
Exploit human decision-making and cognitive biases to craft more effective attacks. - Building relationships
Get victim more friendly and comfortable to enhance trust level. - Motivation
Motivate target to take action
There are some motivation techniques, namely :
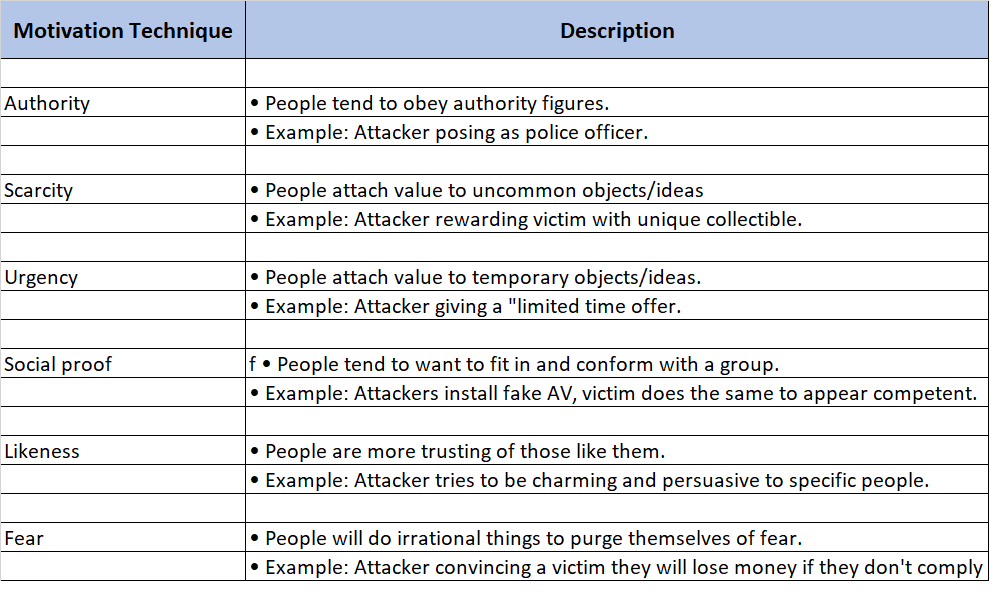
Fig 1. Motivation Techniques
-
Phishing
A tactic in which an attacker attempts to obtain sensitive information
from a user by posing as a trustworthy figure through email.
Also used more generally to refer to any such trick over electronic communications.
• One of the most common and effective social engineering tactics.
• Easy to distribute.
• Impersonal.
• Can leverage technical tricks like spoofing FROM headers.
Example:
- The attacker sends an email claiming to be from the victim’s bank.
- Contents tell victims to send their passwords so the account can be reset.
- If the victim doesn’t comply, the bank will terminate the account.
- Leverages urgency and fear as motivators.
- The victim receives email with spoofed headers and thinks it’s legitimate.
- Victim complies with the fraudulent request.
Types of Phishing :
A. SMiShing
- Phishing is done over text messages (SMS).
- Users may ignore unknown texts more readily than email.
B. Vishing
- Phishing is done over telephone/VoIP.
- Real-time voice conversations can generate more trust.
C. Pharming
- Phishing entices users through a spoofed website.
- The victim interacts with the site to provide info.
D. Spear phishing
- Phishing that targets specific individuals or groups.
- Customized messages are more effective.
E. Whaling
- Spear phishing that targets wealthy and/or powerful people.
- High risk, high reward.
F. Impersonation
- Many social engineering attacks use impersonation.
- It relies on the target not being able to identify the attacker.
- Example: Attacker pretends to be a help desk worker.
-
- Calls employees and asks for their password.
- Target may be less suspicious if they don’t know who works at the help desk.
- Can be more effective in face-to-face interactions.
-
- People want to avoid appearing rude or dismissive.
- May be less likely to question an impostor.
- Relies on the target not knowing what the real person looks like.
G. Elicitation
Is a technique used to gather information discreetly? That is to say; elicitation is the strategic use of casual conversation to extract information from people (targets) without giving them the feeling that they are being interrogated or pressed for the information. Elicitation attacks can be simple or involve complex cover stories, planning, and even co-conspirators. Social engineers use elicitation techniques to gather valuable information and use the intel during the development of a larger Social Engineering campaign.
H. Hoaxes
An element of social engineering in which the attacker presents a fictitious situation as real. A hoax is a message that deceives people into thinking that something is true when it isn’t. Hoaxes can be rumors, urban legends, pseudoscience, or April Fools’ stories that are accepted as truth. Back in the 17th-century, to hoax meant “to cheat.” The essence of the word hasn’t changed much since.
I. Baiting
Baiting is a social engineering attack in which an attacker leaves physical media in
a location where someone else might pick it up and use it.Through this method of social engineering attack, which entails using the victim’s own curiosity against them, hackers are able to persuade their victims to open dangerous links by luring them with offers of free music or movie downloads. They can also create free software advertisements that direct their victims towards other malicious content and encourage them to download applications that have been infected with malware.
J. URL Hijacking / Typosquatting
Typosquatting, or URL hijacking, is a form of cybersquatting targeting people that accidentally mistype a website address directly into their web browser URL field. Cybersquatters register domain names that are a slight variation of the target brand (usually a common spelling error.
Typosquatting comes into picture when such typographical errors is made by the Internet users. If a user accidentally enters a wrong website address into the browser, the entered address may redirect the user to an alternate website that is usually designed by the hackers for malicious purposes. The alternate website owner gets free traffic. The hackers usually target well-known domains like Facebook, Google etc.
Causes of Typosquatting:
-
- Enter the misspelled domain name into the browser.
- Enter the wrong domain extension (such as .com instead of .org).
- Forget to include hyphen for a domain that includes a hyphen [NOTE: hyphen is the only special character allowed in the IDNS].
- Spelled differently from the registered one (such as colour instead of color).
Threats of Typosquatting:
All kinds of Internet theft is possible through Typosquatting. It can be very dangerous if the URL of a misleading domain is being entered. It can:
-
-
- Redirect to an alternate website used for a malicious purpose such as phishing.
- Install malware or Ransomware to the PC without even clicking on the site.
- Steal confidential data of the Internet users such as credit card information.
- Steal the identity of the users for the purpose of Identity theft.
- Expose the users to Internet pornography.
-
Preventive Measures:
It is highly recommended to be careful while typing the domain name of a website. Apart from that, the following ways can be adapted to avoid typo-squatting.
-
-
- Bookmark or Pin Tab the websites that are frequently visited.
- Speech recognition softwares can be used to visit popular URLs such as www.google.com.
- Perform web searches and then click on the intended site from the web search results.
- Keep the antivirus software updated.
- Never click links in chats, messages, emails provided by suspicious senders.
- If you own a domain, try to register its typo versions before the hackers.
-
K. SPAM, SPIM and SPIT
Spamming is the use of messaging systems to send an unsolicited message (spam) to large numbers of recipients for the purpose of commercial advertising, for the purpose of non-commercial proselytizing, or for any prohibited purpose (especially the fraudulent purpose of phishing). SPIM is SPAM over internet messaging such as Whatsapp and so on, and SPIT is SPAM over the telephone, in Indonesia people often to get phone for somebody for insurance, financial aid, or even gift, that actually fake.
L. Shoulder Surfing
In computer security, shoulder surfing is a type of social engineering technique used to obtain information such as personal identification numbers (PINs), passwords and other confidential data by looking over the victim’s shoulder, either from keystrokes on a device or sensitive information being spoken and heard, also known as eavesdropping.[1][2].
M. Tailgating
Tailgating (also known as piggybacking) is one of the most widespread security breaches affecting businesses today and often goes undetected. Tailgating can be simply described as the passage of unauthorized personnel, either forced or accidental, behind that of an authorized user. The difference between tailgating and piggybacking is in piggybacking the target is know that somebody is following him.
Guidelines for Conducting Social Engineering Test
- Understand basic components of social engineering.
- Leverage motivation techniques.
- Launch a phishing attack to entice targets to leak sensitive info.
- Use media other than just email for phishing.
- Create a convincing forgery of a popular website.
- Capture credentials through login forms on the forged website.
- Leverage gathered data about people to spear phish specific targets.
- Consider targeting high-level personnel in phishing.
- Use impersonation to make attacks seem more authentic.
- Use elicitation to get targets to reveal info.
- Leverage hoaxes to make attacks more convincing.
- Drop a USB drive loaded with malware in a parking lot.
- Determine how users fall victim to mistyped URLs.
- Leverage spam techniques in phishing attacks.
- See how easy it is to observe employees without their knowledge.
- Consider how the environment might make tailgating/piggybacking more/less effective.
Besides everything that has been mentioned above, we have to consider physical factors as well, such as :
- Door/hardware locks.
- Surveillance cameras.
- Security guards.
- Lighting that makes nighttime intruders visible.
- Fences, gates, and other physical barriers.
- Mantraps.
- Alarms and motion sensors.