One process that has been clearly described in the previous post for conducting active reconnaissance is Enumeration. One important activity is how can we reveal the subdomain information, so we will have better information about online information that a company or organization gives to the public.
So, we will try to gather the subdomain and we will make a subdomain scanner with python in this post. For making a subdomain scanner, we need a library call request, that has to be installed in our system.
First of all, we install the request library by launching the command as follows :
pip3 install requests
The method we gonna use here is brute-forcing, in other words, we gonna test all common subdomain names of that particular domain, whenever we receive a response from the server, that’s an indicator for us that the subdomain is alive
import requests # the domain to scan for subdomains domain = "google.com"
Now we gonna need a big list of subdomains to scan, I’ve used a list of 100 subdomains just for demonstration, but in the real world, if you really want to discover all subdomains, you gotta use a bigger list, check this github repository which contains up to 10K subdomains.
I have a file “subdomains.txt” in the current directory, make sure you do too (grab your list of your choice in this repository):
# read all subdomains
file = open("subdomains.txt")
# read all content
content = file.read()
# split by new lines
subdomains = content.splitlines()
Now subdomains list contains the subdomains we want to test, let’s brute-force:
# a list of discovered subdomains
discovered_subdomains = []
for subdomain in subdomains:
# construct the url
url = f"http://{subdomain}.{domain}"
try:
# if this raises an ERROR, that means the subdomain does not exist
requests.get(url)
except requests.ConnectionError:
# if the subdomain does not exist, just pass, print nothing
pass
else:
print("[+] Discovered subdomain:", url)
# append the discovered subdomain to our list
discovered_subdomains.append(url)
First, we build up the URL to be suitable for sending a request, then we use requests.get() function to get the HTTP response from the server, this will raise a ConnectionError exception whenever a server does not respond, that’s why we wrapped it in a try/except block.
When the exception wasn’t raised, then the subdomain exists. Let’s write all the discovered subdomains to a file:
# save the discovered subdomains into a file
with open("discovered_subdomains.txt", "w") as f:
for subdomain in discovered_subdomains:
print(subdomain, file=f)
Here is a part of the result when I ran the script:
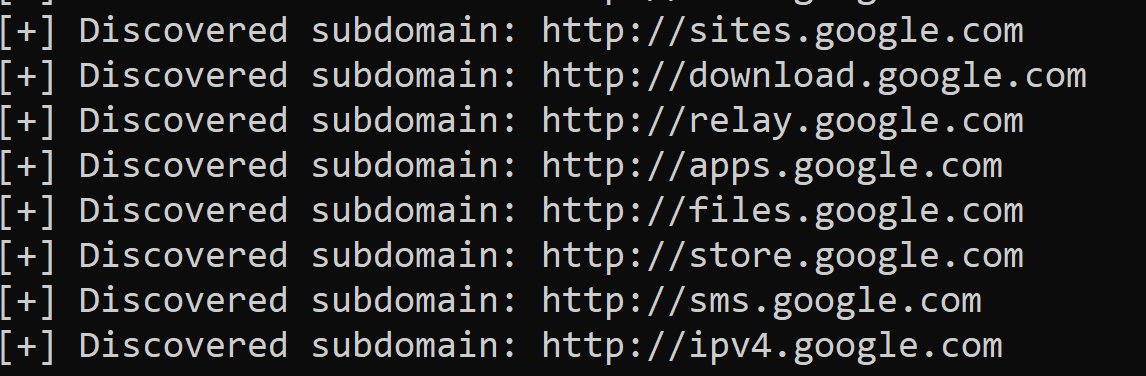
Once it’s finished, you’ll see a new file discovered_subdomains.txt appears, which includes all the discovered subdomains!
Alright, we are done, Now you know how to discover subdomains of any website you really want!